Fiddler usually works out of the box, with a few exceptions. One of those exceptions is capturing traffic from a JVM.
To capture plain HTTP traffic from a JVM, you can configure Fiddler as the proxy by setting these VM args:
-DproxySet=true -DproxyHost=127.0.0.1 -DproxyPort=8888
[Note: Fiddler proxies at port 8888 by default]
Capturing HTTPS traffic (of course, to view it unencrypted in Fiddler), is slightly more involved. Here’s how to do that.
1. Export Fiddler’s Root Certificate
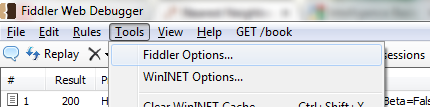
Click on Tools -> Fiddler Options… to open the Fiddler Options dialog.
Switch to the HTTPS tab, and click on Export Root Certificate to Desktop.
This will generate the file: FiddlerRoot.cer on your Desktop.
2. Create a JVM Keystore using this certificate
This step will require Administrator privileges (since keytool doesn’t seem to work without elevating privileges). So, open command prompt as Administrator, by right clicking on the Command Prompt icon, and clicking on Run as administrator.
Run the following command (replacing <JAVA_HOME> with absolute path to the JDK/JRE that you’re interested in capturing traffic from):
<JDK_Home>\bin\keytool.exe -import -file C:\Users\<Username>\Desktop\FiddlerRoot.cer -keystore FiddlerKeystore -alias Fiddler
This will prompt you to enter a password. Remember the password, as it’s required for the next step.
Once a password is entered, this’ll create a file called FiddlerKeyStore. Remember the path to this file, as we’ll be using it in the next step. You can, of course, move it to a more convenient location and use that path.
3. Start the JVM with Fiddler as the proxy, and the Keystore you just created as a Trust Store
Essentially, we’re asking the JVM to use Fiddler as the proxy, and to trust the keys in the Keystore we just created. Here’re the VM args to configure your Keystore as the Trust Store:
-Djavax.net.ssl.trustStore=<path\to\FiddlerKeystore> -Djavax.net.ssl.trustStorePassword=<Keystore Password>
So, in effect, these are the VM args you’ll need:
-DproxySet=true -DproxyHost=127.0.0.1 -DproxyPort=8888 -Djavax.net.ssl.trustStore=<path\to\FiddlerKeystore> -Djavax.net.ssl.trustStorePassword=<Keystore Password>
That’s about it. Now, launch Fiddler, and launch your JVM (your Java application). Fiddler will start showing all HTTPS (and HTTP) traffic from the JVM in plaintext.
Setting up VM args in an IDE
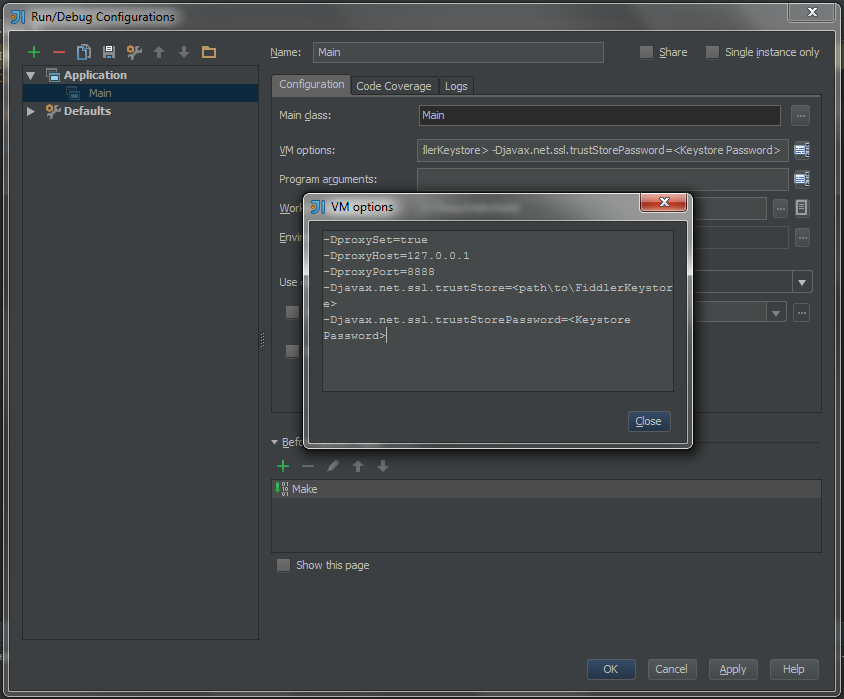
If you’re using IntelliJ or Eclipse for development, you can set VM args in the Run Configuration dialogs. Here’s what they look like with the VM args populated:
Here’s the IntelliJ Run Configuration dialog with the VM args populated:
And here’s the Eclipse Run Configuration dialog with the VM args populated:
[PS: This post is based on one of my SO answers: http://stackoverflow.com/questions/8549749/how-to-capture-https-with-fiddler-in-java/8588914#8588914]


Apparently the syntax doesn’t mean what I think it means. I substituted “C:\Program Files\Java\jre-9.0.1\lib\security\Fiddlerkeystore” and continue to get SunCertPathBuilderException: unable to find valid certification path to requested target
Any ideas?
Same here, did you by chance find a solution?
I even added the Fiddler.crt to cacerts but keep getting
SunCertPathBuilderException: unable to find valid certification path to requested target
One piece of code within my web app uses an Apache library to directly call a cgi script on an yonder server. Can I capture that request, modify it and then send it further on
Hi
Thanks for your good article.This solution has worked in my local pc, but not work in Windows Server 2008… do you have any solution?
thanks for your attention.
Thank you so much! I was making a request to a rest service and this just saved me.
God Bless YOU!!!!!!!!!!!!!!!!!!!!!